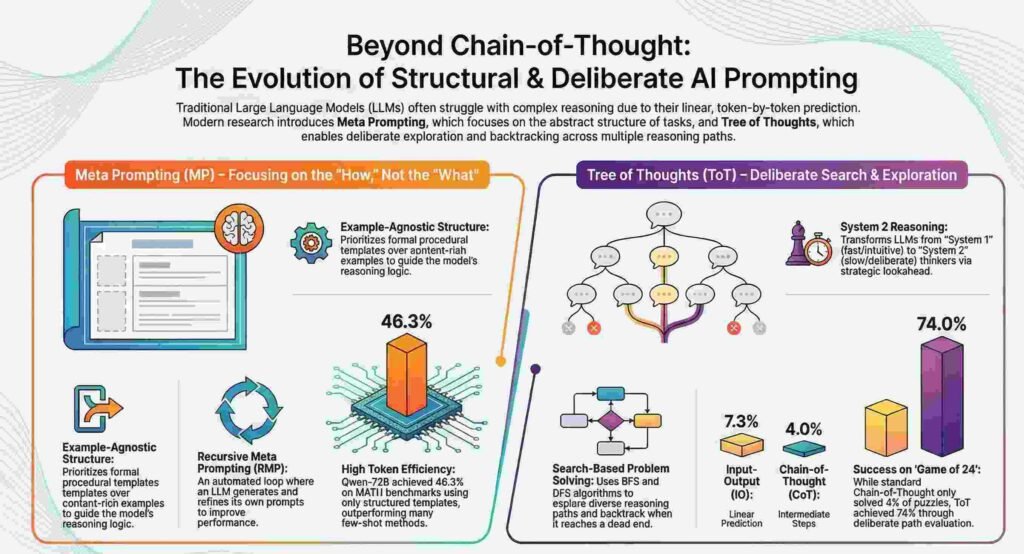
Beyond Next-Token Prediction: 5 Surprising Shifts Redefining How AI Thinks
1. The “System 1” Problem Modern Large Language Models (LLMs) are defined by an autoregressive…
5 Takeaways- From Nano Banana 2 – Redefining AI Art
Nano Banana 2 Google AI Image Model Nano Banana 2 is Google’s advanced AI image…
The Great Decoupling: Architecting Relevance in the Era of Agentic Commerce and Synthetic Discovery
1. The End of the “Ten Blue Links” The digital discovery landscape has reached a…
Beyond the Hype: 5 Uncomfortable (and Impactful) Realities of the AI Era in 2026
In 2026, the honeymoon phase of the AI revolution has ended, leaving us with a…
Exciting Developments in Robotics
Robotics is making big news around the globe. Here are some key points about the…
Tech News Today Feb 6th 2026
Big Tech Massive AI Infrastructure Spending Triggers Market Volatility.Projected spendings of Big Tech companies in…
What is Clawdbot? Clawdbot macOS Quick Install: Step-by-Step Terminal Guide
Clawdbot, First Rebranded As Moltbot, and finally Fixed on OpenClaw The history of the AI assistant…
Amazon Great Republic Day Sale 2026: Dates, Top Deals, and Must-Know Tips
Amazon’s Great Republic Day Sale kicks off on January 16, 2026, bringing massive discounts on…
Forget the Chatbots: 4 Surprising AI Trends That Will Define 2026
When most people think of artificial intelligence, their minds jump to high-profile chatbots like ChatGPT…