What Are Wi-Fi Attacks?
Wi-Fi attacks refer to exploits and hacking attempts against wireless networks. Hackers can use readily available tools and software to intercept wireless traffic, steal data, gain unauthorized access, and launch denial of service attacks. The most common targets are Wi-Fi routers, access points, connected devices and users connected to public hotspots.
Types of Wi-Fi Attacks
Some common Wi-Fi attack types include:
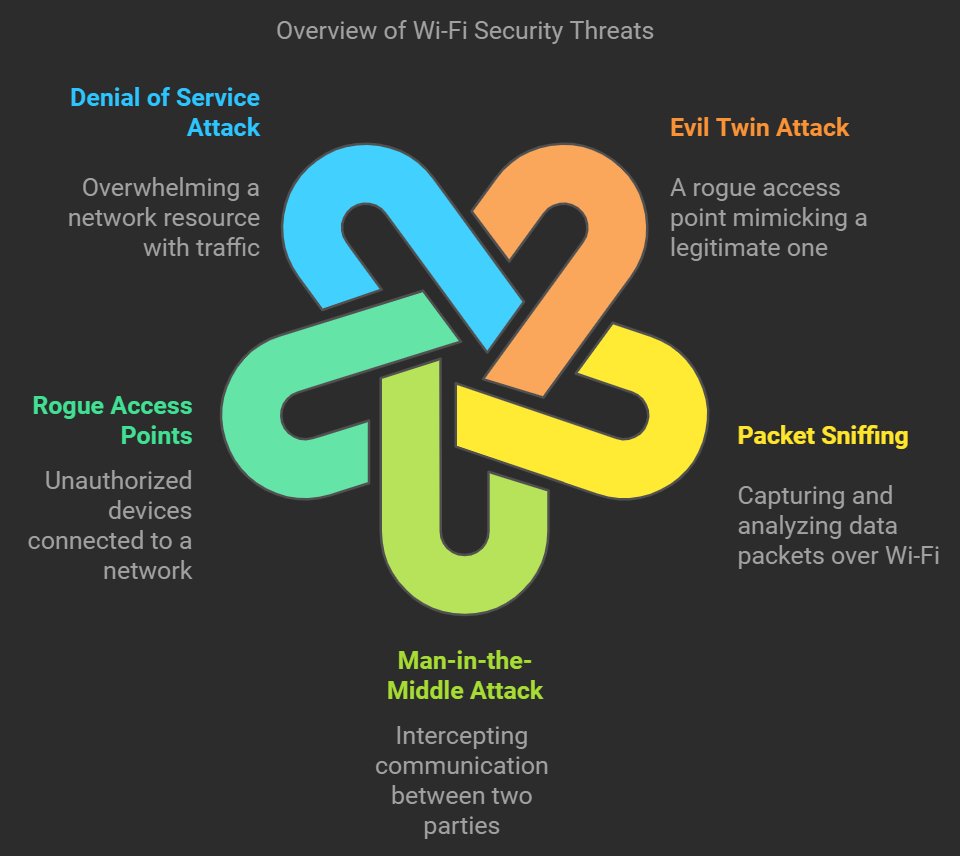
- Wardriving – Driving around with a laptop and Wi-Fi card to find wireless networks. Used to gather info to access networks.
- Evil Twin – Setting up a fake malicious Wi-Fi hotspot with same name as a legitimate network to trick users.
- Denial of Service – Flooding network with traffic to disrupt connectivity for legitimate users.
- Man-in-the-Middle – Intercepting communications between devices by routing traffic through attacker’s computer.
- Cracking – Guessing or brute forcing the password to gain unauthorized access.
- Packet Sniffing – Using a packet analyzer to intercept wireless traffic and steal data like credentials.
How Wi-Fi Attack Works
The hacker interrupts the connection between the router and a client. This can be the basis for most Wi-Fi network attacks, including the Evil Twin and brute force attacks. The hacker can also continuously send deauthentication packets to the client, causing a Denial-of-Service (DoS).
Brute Force Attack:
How it Works: The attacker tries to guess the Wi-Fi password by intercepting data traffic during the login.
Defending against brute force involves rate limiting login attempts, locking accounts after a certain number of incorrect logins, using multi-factor authentication, or making password requirements more complex.
Evil Twin Attack:
How it Works: Starts with a deauthentication attack. The hacker sets up a rogue Wi-Fi network to mimic the real one and intercepts the data traffic.
Common defenses include using VPNs over public WiFi, checking for certificate warnings in the browser, being alert to subtle differences in network names, and avoiding sensitive transactions on public networks.
General Wi-Fi Attacks:
Attacking the Wi-Fi Connection: Hackers record data exchanged via Wi-Fi to guess the Wi-Fi key, gaining access to sensitive information.
Attacking the Router Directly: Allows hackers to manipulate smart home devices, encrypt data via ransomware, or make the router part of a botnet.
How to Fight Wi-Fi Attacks:
Increase Router Protection: Enhance the security settings of your router to make an attack too costly for the hacker.
Stay Informed: Keep yourself updated about security gaps and address them with firmware updates.
Consequences of Wi-Fi Attacks:
Data Theft: Hackers can steal sensitive information like online banking passwords.
Illegal Activities: Attackers can use your internet access to carry out criminal acts that trace back to you.
Smart Home Manipulation: Hackers can control smart home devices or encrypt data to demand a ransom.
Recognizing the Signs
Indications of a Wi-Fi Attack
Signs that a Wi-Fi network may be compromised:
- Slow internet speeds and intermittent connectivity
- Unknown Wi-Fi networks appearing
- Failing to connect to known Wi-Fi networks
- Unusual activity on online accounts accessed via Wi-Fi
- Antivirus warnings of network threats detected
Common Attack Vectors
How attackers gain entry:
- Unsecured routers with default passwords
- Routers with old vulnerable firmware
- Public hotspots without encryption
- Wireless users connecting to unsecured networks
- Open or WEP encrypted networks
- WPS Pin vulnerability
- Known passwords and dictionaries
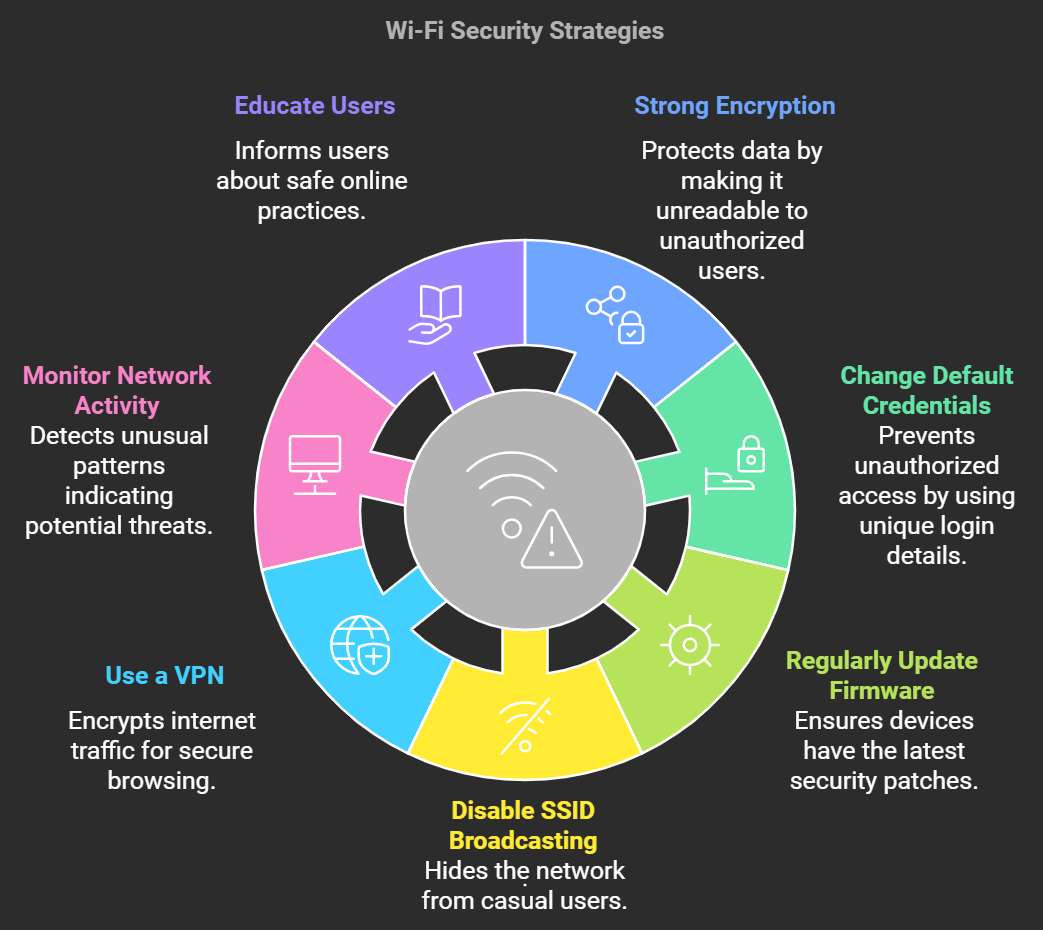
Protecting Your Wi-Fi Network
Strengthening Wi-Fi Security
Steps to secure Wi-Fi networks:
- Change default router password
- Enable WPA2 or WPA3 encryption
- Use a strong Wi-Fi password
- Disable WPS
- Update router firmware
- Enable firewall on router
- Hide SSID
- Use MAC address filtering
- Separate guest network
Essential Security Measures
Vital security practices:
- Strong Wi-Fi encryption like WPA2
- Unique strong Wi-Fi password
- Router firewall enabled
- Firmware updated
- MAC address filtering
- Disabled remote management
- SSID broadcasting disabled
Tools for Wi-Fi Attack Detection
Wi-Fi Scanning Software
Tools to detect attacks:
- NetStumbler – Common Wi-Fi scanner
- inSSIDer – Scans for networks and tests security
- Wireshark – Network analysis and packet capturing
- Kismet – Network sniffer and intrusion detection
Intrusion Detection Systems
DEDICATED IDS Systems:
- Snort – Open source IDS with wireless rulesets
- Suricata – IDS engine that can analyze 802.11 traffic
- Security onion – Linux distro for IDS, network security
- AirDefense – Commercial wireless IDS/IPS solution
Preventing Wi-Fi Attacks
Encryption and Authentication
Preventive measures:
- Use WPA2 PSK or WPA2 Enterprise Wi-Fi encryption
- Employ RADIUS for authentication
- Use a wireless intrusion prevention system
- Leverage wireless MAC filtering
- Disable unused wireless functions like WPS
Network Segmentation
Network separation best practices:
- Separate wireless network into its own VLAN
- Use client isolation to prevent wireless client interactions
- Enable AP isolation to keep access points separated
- Segment IoT devices on separate network
Wi-Fi Attack Case Studies
Real-Life Examples
- Researchers cracked WPA2 security in 2017 using key reinstallation attacks
- Wi-Fi sniffing attack hit thousands of hotel guests across the world
- Devil’s Ivy attack exploited flaws in wireless IP cameras
Lessons Learned
These incidents revealed:
- Importance of updating devices and software
- Vulnerabilities in encryption protocols like WPA2
- Insecure devices like IP cameras can compromise Wi-Fi
- Public Wi-Fi hotspots are prime targets for attackers
Securing Your Smart Devices
IoT Vulnerabilities
IoT introduces new threats:
- Default passwords on connected devices
- Lack of firmware updates and encryption
- New attack surfaces and vectors
- Exposed services and ports
Best Practices
Securing IoT:
- Change default credentials
- Perform firmware updates
- Disable unnecessary services
- Use separate VLAN for IoT
- Use encryption like WPA2
Wi-Fi Attack Trends
Emerging Threats
Evolving attack techniques:
- Targeting WPA3 and Wi-Fi 6
- Abusing IoT device vulnerabilities
- Attacking open source Wi-Fi tools and libraries
- Leveraging AI to automate attacks
Future Projections
Expected developments:
- Growth of crowdsourced wardriving mapping
- More focus on attacking enterprise networks
- Rise of Wi-Fi phishing and evil twin attacks
- Easier abuse of vulnerabilities with attack toolkits
Expert Interviews
Security Professional Insights
Industry experts recommend:
- “Make sure you keep your router firmware up to date, use super strong and unique passwords for your Wi-Fi, and at the very least, make use of WPA2 encryption..”
- “Monitor connected devices and beware of unauthorized users. Make use of wireless intrusion detection systems.”
Recommendations
Experts suggest:
- “Use ethical hacking techniques like penetration testing to identify Wi-Fi vulnerabilities before attackers do.”
- “Isolate and segment wireless access to limit exposure. Don’t allow wireless access to sensitive systems.”
Take Action Now
Steps to Secure Your Wi-Fi
Easy ways to start securing Wi-Fi network:
- Change Wi-Fi password from default
- Update router firmware to latest version
- Turn on WPA2 encryption in router settings
- Disable remote management on router
Stay Safe Online
General tips:
- Avoid public open Wi-Fi networks when possible
- It is recommended to utilize a Virtual Private Network (VPN) when accessing public hotspots.
- Monitor accounts and devices accessed over Wi-Fi for unusual activity
- Use encrypted internet connections as much as possible
Here are some tips for dealing with dangerous Wi-Fi attacks and protecting yourself:
- Use WPA2 or WPA3 encryption on your wireless network. Avoid using outdated WEP encryption which is easy to crack. Set a strong and unique password.
- Don’t use public open Wi-Fi networks for sensitive browsing. Anything you send can potentially be intercepted. Use a VPN if you need to use public networks.
- Disable Wi-Fi auto-connect so your devices don’t automatically join networks without your knowledge. This prevents attacks through rogue access points.
- Update router and device firmware regularly to patch security vulnerabilities. Obsolete software presents a vulnerable target..
- Turn off Wi-Fi functionality if not in use. Keep an eye out for unknown networks your device may have connected to without you realizing.
- Use a firewall and antivirus software to block and detect malware and network intrusion attempts.
- Disable WPS on your router if possible. WPS lets attackers easily brute force their way in.
- Monitor network traffic and connected devices to your network to detect any unusual activity that could indicate an attack.
- Physically secure your Wi-Fi router and don’t broadcast the SSID. This makes it harder for attackers nearby.
- Look out for signs of Wi-Fi sniffing or jamming and report if you suspect malicious activity.
Being alert and proactive about Wi-Fi security is key to protecting yourself from common wireless network attacks. Taking measures like using strong encryption, updating devices, monitoring traffic, and being cautious on public Wi-Fi can help keep you safe.
FAQs
Q: What are the most common Wi-Fi attacks?
A: The most prevalent Wi-Fi attacks include evil twin, denial of service, cracking passwords, man-in-the-middle attacks, and packet sniffing.
Q: How can you tell if someone is hacking your Wi-Fi?
A: Signs can include slow internet speeds, inability to connect to Wi-Fi, unknown networks appearing, unusual activity on accounts, and antivirus detecting network threats.
Q: What is the most secure encryption for Wi-Fi?
A: WPA2 is the most secure widely available encryption for Wi-Fi networks today, with the newer WPA3 standard gradually rolling out.
Q: How can businesses protect their Wi-Fi network security?
A: Businesses should use enterprise-grade Wi-Fi equipment, WPA2/WPA3 encryption, RADIUS authentication, wireless intrusion systems, network segmentation, and regular monitoring.
Q: What precautions should users take when connecting to public Wi-Fi?
A: Users should avoid sensitive transactions on public Wi-Fi, leverage a VPN, check for HTTPS on websites, and use two-factor authentication when possible.
Discover more from TechResider Submit AI Tool
Subscribe to get the latest posts sent to your email.
